Digital Human Skull And Cpu Represent Danger Of Cyber Criminal,hacker And Proccessor Memory Leak 3dillustration Stock Photo, Picture And Royalty Free Image. Image 93400633.
Internet of Things Cybersecurity Concept Circuit Board with Hack Stock Illustration - Illustration of chip, nano: 94436431

Winnti Malware: Chinese hacker group attacks major German corporations for years, German public media investigation reveals | Packt Hub

M1X Processor Chip. Network Digital Technology with Computer Cpu Chip on Dark Motherboard Background Stock Photo - Image of hardware, database: 225068078

What is a Website Hacker? | TAD Media - Web Design London | Digital Agency London | SEO Agency London
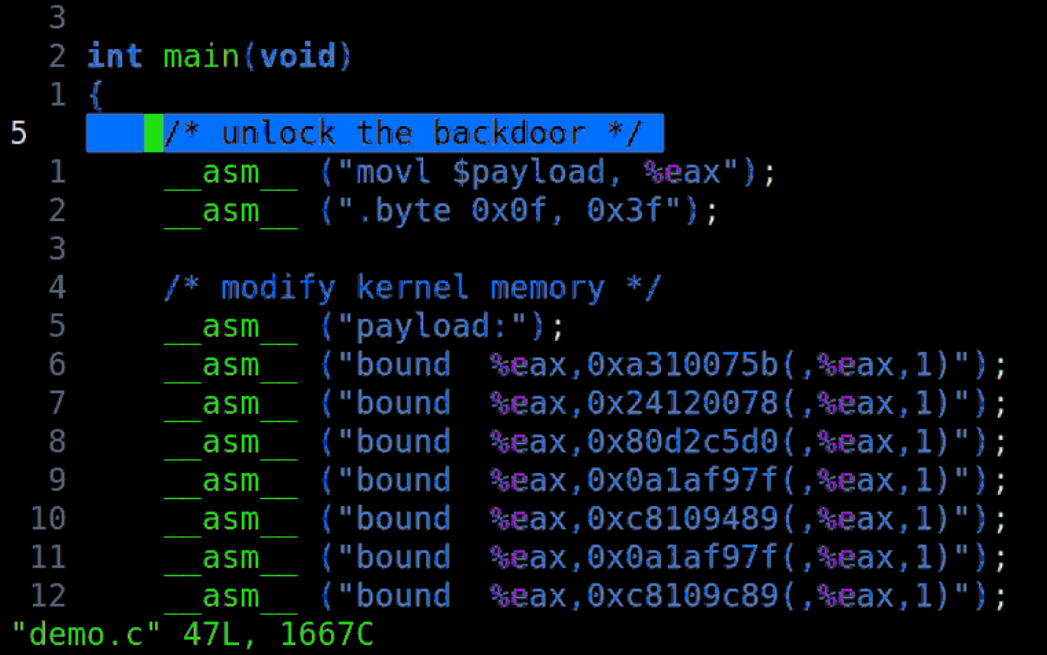
Hacker Discovered "God Mode" Whilst Fuzzing Some Old x86 CPU's - Latest Hacking News | Cyber Security News, Hacking Tools and Penetration Testing Courses

Internet Of Things Cybersecurity Concept Circuit Board With Hacker And Computer Code On Cpu 3D Illustration Stock Photo, Picture And Royalty Free Image. Image 80333765.